#
2FA Migration
2FAuth can import data in various formats to ease you migrate from another 2FA app or to restore a backup. Note that not all 2FA apps enable data export so 2FAuth will never covers all possible migrations.
#
Exporting From
First step is to export data from the 2FA source app in order to get a migration resource, like a file or a QR code. Follow one of the dedicated section below then jump to the
#
Google Authenticator
Open Google Authenticator and use the icon to enter the Export feature.
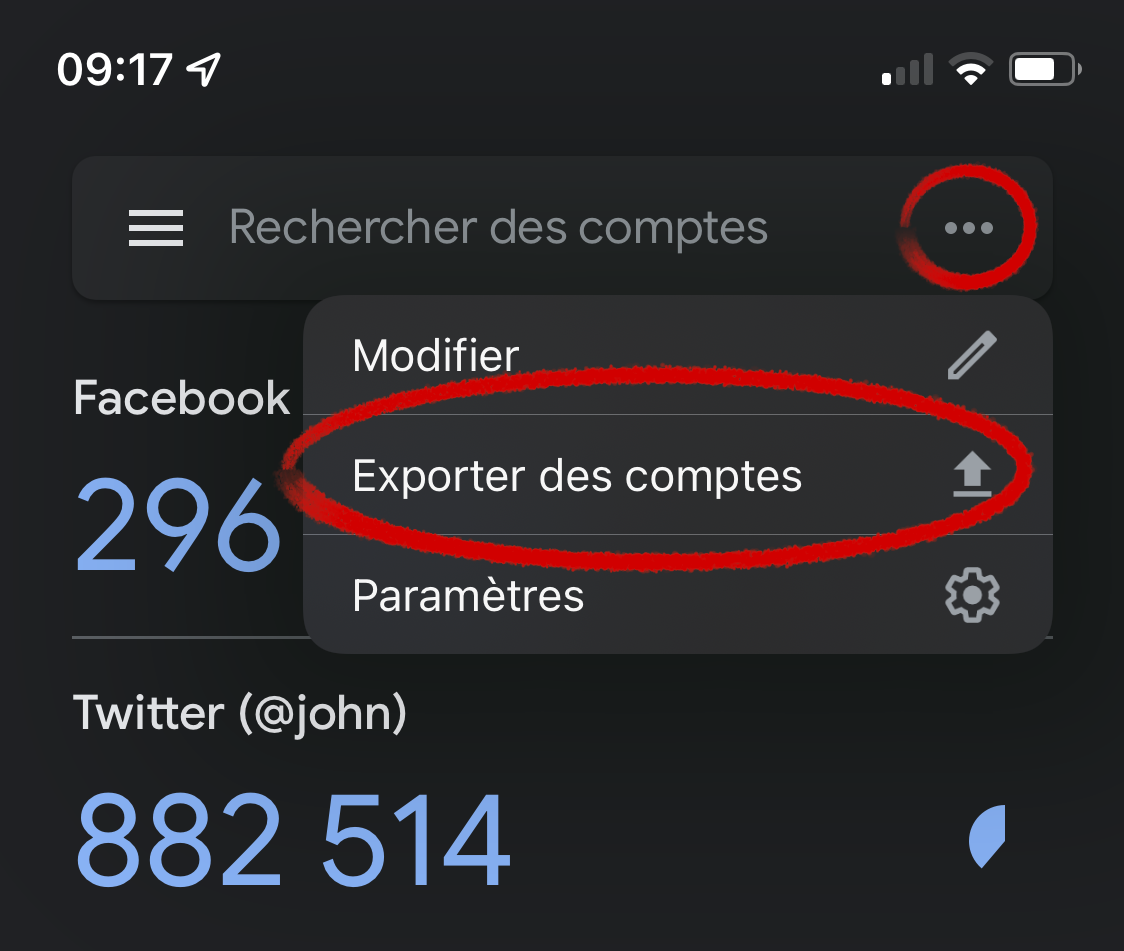
Next choose one or more accounts to export then click the button.
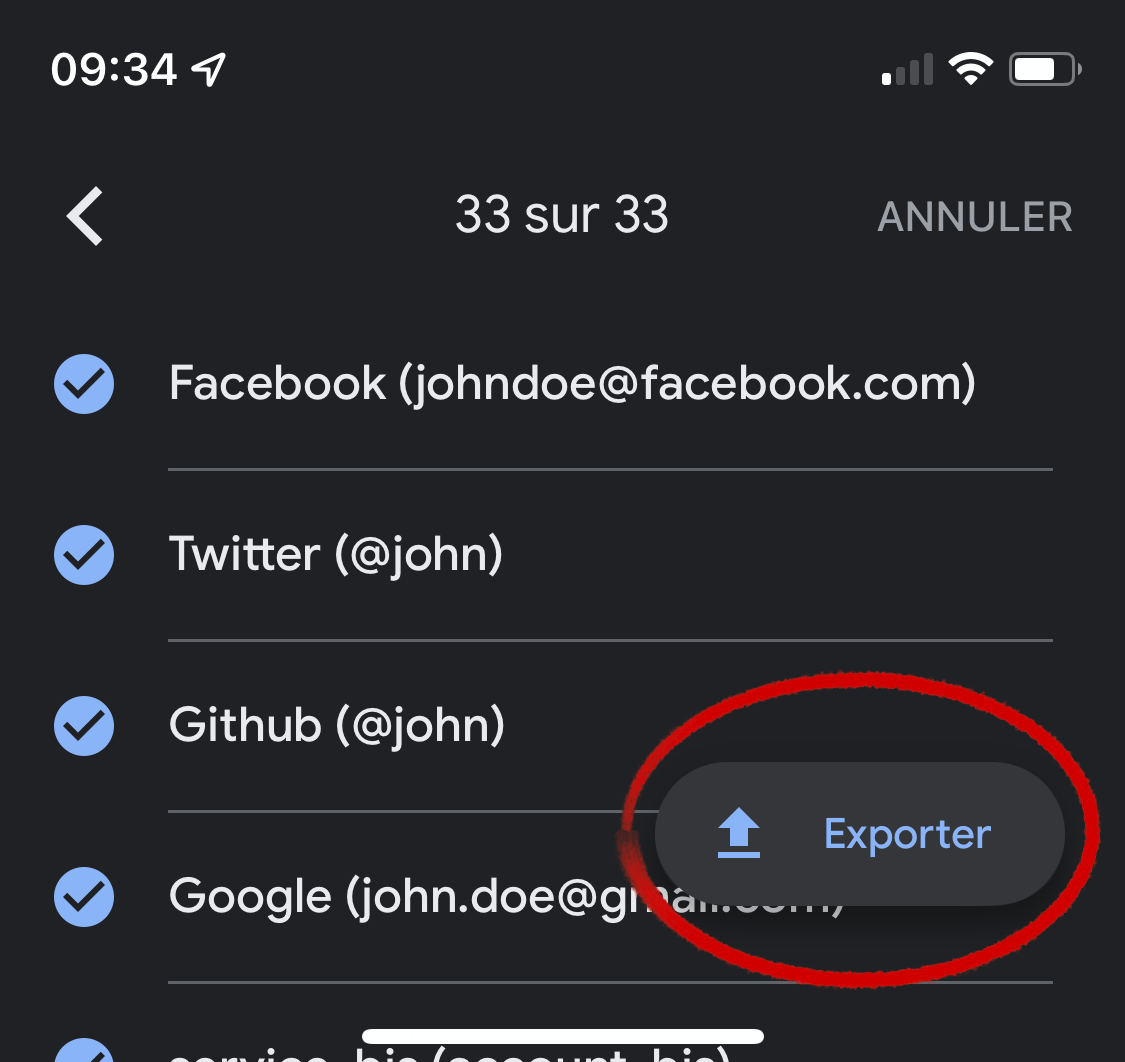
Google Authenticator now displays a QR code to import into 2FAuth. Keep it on screen or save a screen capture for later use or backup.
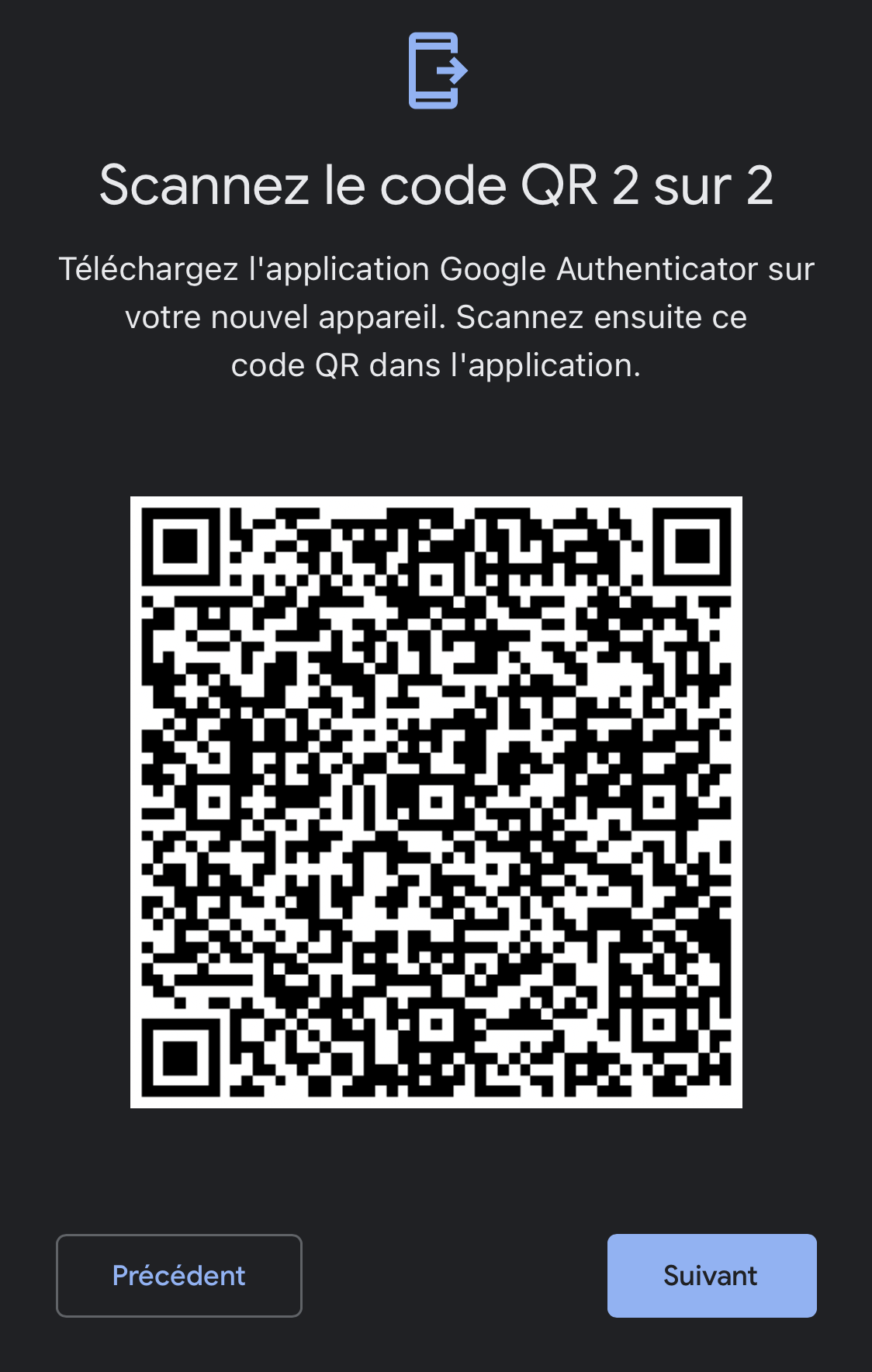
Multiple QR codes
If you choose to export more than 10 2FA accounts, Google Authenticator will generate several QR codes (one by tens).
The Import into 2FAuth process should be executed for each G-Auth QR code.
#
2FAS Authenticator
Open 2FAS Authenticator and enter the Settings section. Then enter the 2FAS Backup feature.
Enter the Export tool.
Uncheck the password option and click the button.
Save (and secure) the .2fas migration file, you are ready to import your accounts into 2FAuth
#
Aegis Authenticator
Enter the Import & Export feature.
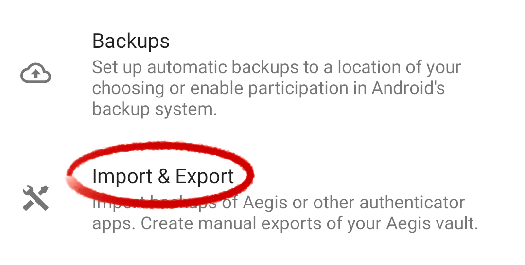
Open the Export tool.
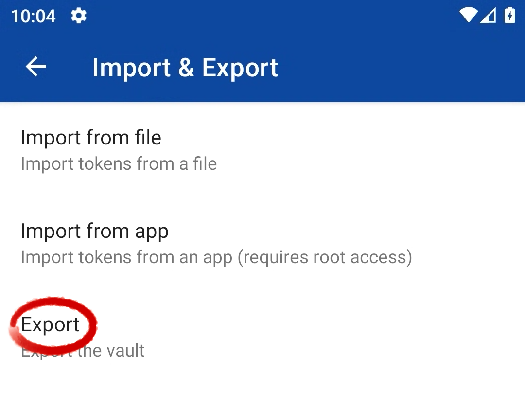
Whatever the export format (both are supported by 2FAuth), uncheck the encryption option and click the OK button.
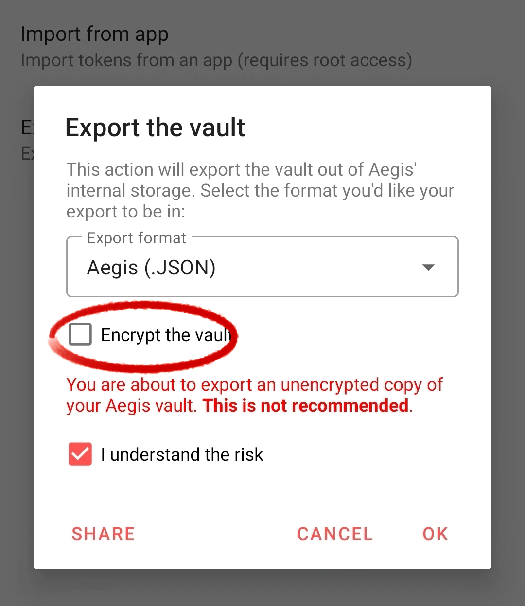
Save (and secure) the migration file, you are ready to import your accounts into 2FAuth
#
Importing into 2FAuth
The import process consists of 2 steps: The preloading (with validation) of the exported data and the recording of all or part of the valid data.
#
Preloading
From the 2FAuth main view:
- Click the button, just as if you had to add a new account
- Click the button in the alternative methods
- Submit your migration resource: a QR code or a file/QR code
2FAuth now lists all accounts found in the migration resource.
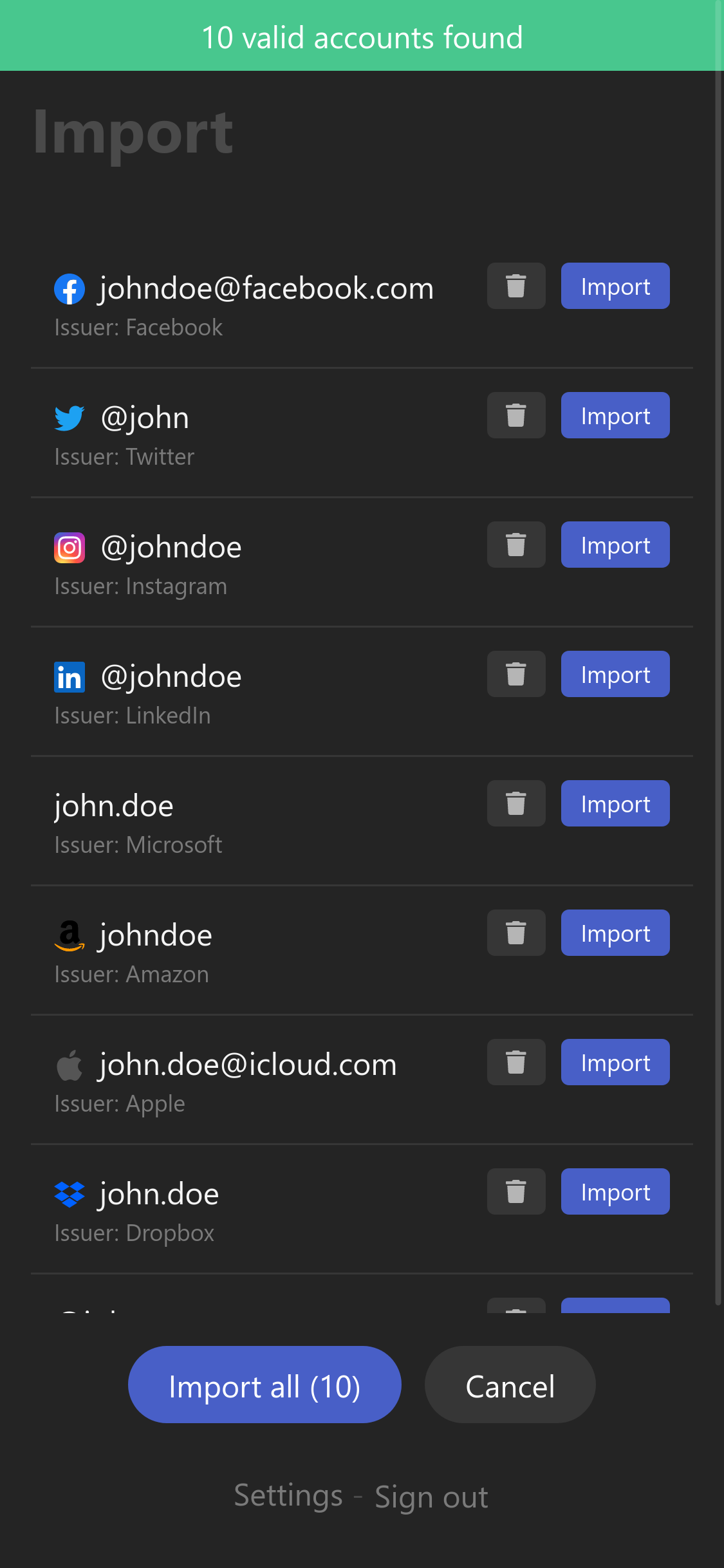
Duplicates
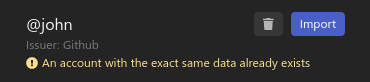
2FAuth checks for possible duplicates by comparing preloaded accounts with existing accounts in its database.
Duplicates are simply flagged, they can still be imported.
Validation
Accounts that do not respect OTP specification are automatically skipped
#
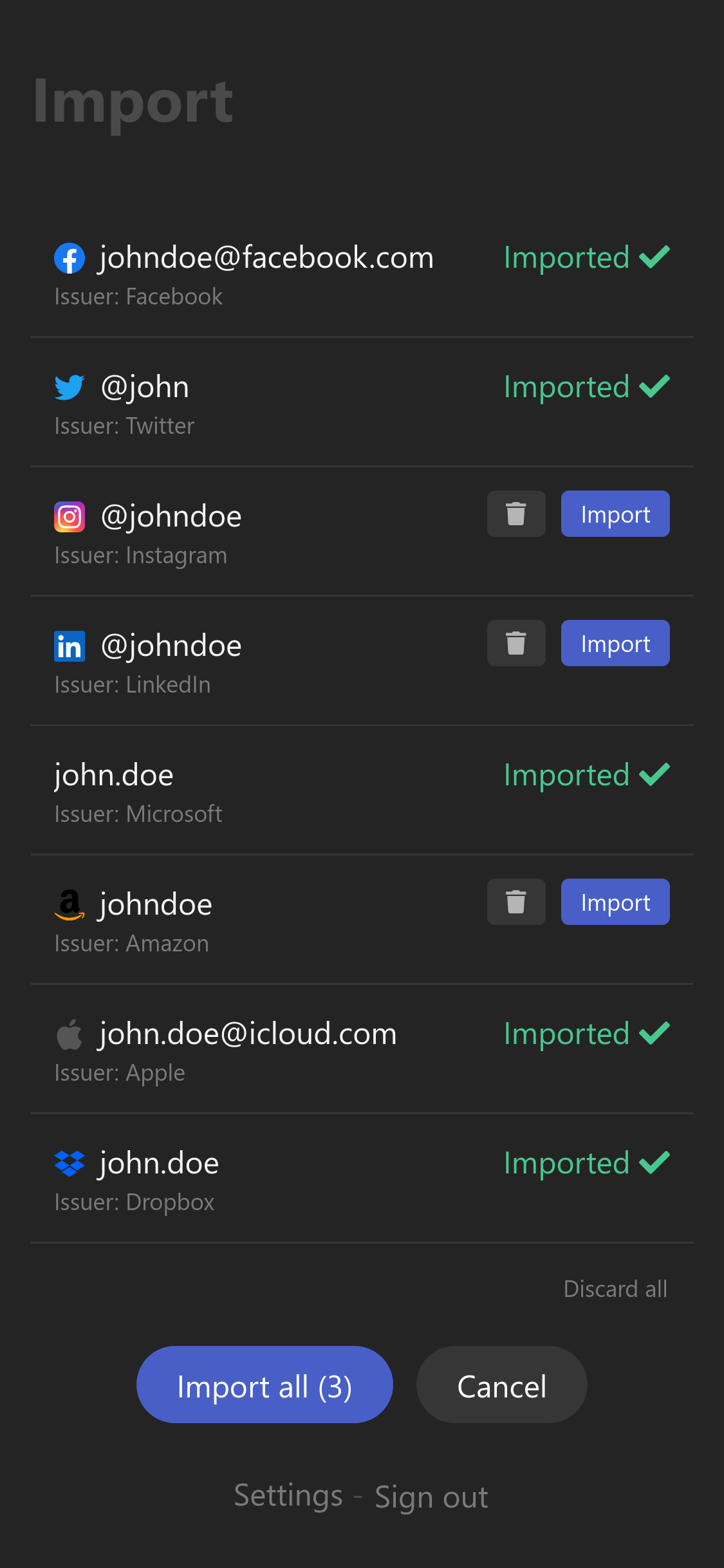
Recording
This final step lets you save the preloaded accounts to the 2FAuth database.
- You are free to record or discard the accounts of your choice.
- Click on account titles to get a fresh OTP if you want to check the integrity of any account.
- Nothing is added to 2FAuth until you click on an button or the button.
#
Exporting from 2FAuth
2FAuth lets you export your 2FA data. This is particulary usefull when you want to create a backup on the fly or to migrate to another 2FA app.
#
Selective export
From the main view of 2FAuth, click the button to switch to Edit mode. You will then be able to select the 2FA accounts that you want to export. Use the button of the view toolbar to select all of them in a click.
Once your selection is done, click the button. You will be prompt to download a migration file in JSON format.
2FAuth supports importing its own migration resource. See
#
Export schema
2FAuth uses its own JSON schema to structure the exported data.
{
"$schema": "https://json-schema.org/draft/2020-12/schema",
"title": "2FAuth Export",
"description": "2FA data export by 2FAuth",
"type": "object",
"properties": {
"app": {
"description": "The 2FAuth version used to export the data",
"type": "string"
},
"schema": {
"description": "The schema version",
"type": "integer"
},
"datetime": {
"description": "Datetime of the export",
"type": "string"
},
"data": {
"description": "A collection of 2FA items",
"type": "array",
"items": {
"type": "object",
"description": "A single 2FA item",
"properties": {
"otp_type": {
"description": "The OTP type of the 2FA item",
"enum": ["totp", "hotp", "steamtotp"]
},
"account": {
"description": "The identifier of the account protected by the 2FA item",
"type": "string"
},
"service": {
"description": "The issuer of the 2FA item",
"type": "string"
},
"icon": {
"description": "The filename of the 2FA item's icon",
"type": "string"
},
"icon_mime": {
"description": "The mimetype of the 2FA item's icon",
"type": ["string", "null"]
},
"icon_file": {
"description": "A base64 encoded representation of the 2FA item's icon",
"type": ["string", "null"]
},
"secret": {
"description": "The 2FA item's secret",
"type": "string"
},
"digits": {
"description": "The number of digits of the generated OTP",
"type": "integer"
},
"algorithm": {
"description": "The algorithm used to generate OTP",
"enum": ["sha1", "sha256", "sha512", "md5"]
},
"period": {
"description": "The validity period of the generated TOTP",
"type": ["integer", "null"]
},
"counter": {
"description": "The counter of the generated HOTP",
"type": ["integer", "null"]
},
"legacy_uri": {
"description": "The original OTPAUTH URI as provided by the issuer",
"type": "string"
}
}
}
}
}
}{
"app": "2fauth_v5.1.1",
"schema": 1,
"datetime": "2024-04-07T12:16:29.606564Z",
"data": [
{
"otp_type": "totp",
"account": "johndoe@facebook.com",
"service": "Facebook",
"icon": "82yCBkDNghIMJ0RfTkFHLPGFaEZSimAWPB4PMVhT.png",
"icon_mime": "image\/png",
"icon_file": "iVBORw0KGgoAAAA[...]RU5ErkJggg==",
"secret": "A4GRFTVVRBGY7UIW",
"digits": 6,
"algorithm": "sha1",
"period": 30,
"counter": null,
"legacy_uri": "otpauth:\/\/totp\/Facebook%3Ajohndoe%40facebook.com?issuer=Facebook&secret=A4GRFTVVRBGY7UIW"
}
]
}